How Does Financial Planning Work?
Financial Planning
Financial Planning is an ongoing process where we aim to understand your life, and your money and then we work together to connect your money to your life.
We start by creating a single picture of your entire financial life, that shows how the pieces fit together; a financial map.
The next step is a process to identify your goals and create a vision for this new and exciting phase of your life; Your Best Retirement.
Strategies for achieving the goals are developed, preferred approaches are selected from the available alternatives, and then we help you to implement your plan. A plan document on a shelf will not achieve your goals.
Ongoing support ensures that you stay on track, and allows for any needed adjustments as you implement your plan.
You will find everything in one place on your personal financial website, Right Capital. Net Worth, Goals, Income Sources, Expenses, Taxes, Investments, Estate Plan, Insurance & Secure Document storage.
How Does Investment Management Work?
Investment Management
An investment management plan will be tailored to your specific needs and goals, which is why it works best as part of a comprehensive financial plan.
Together we will create an investment plan that helps you to achieve your goals, and supports your lifestyle, while also letting you sleep well at night.
We will develop an asset allocation strategy, and specific investment portfolio recommendations, that are designed to achieve your goals.
We will implement your Investment Strategy and keep it on track for you.
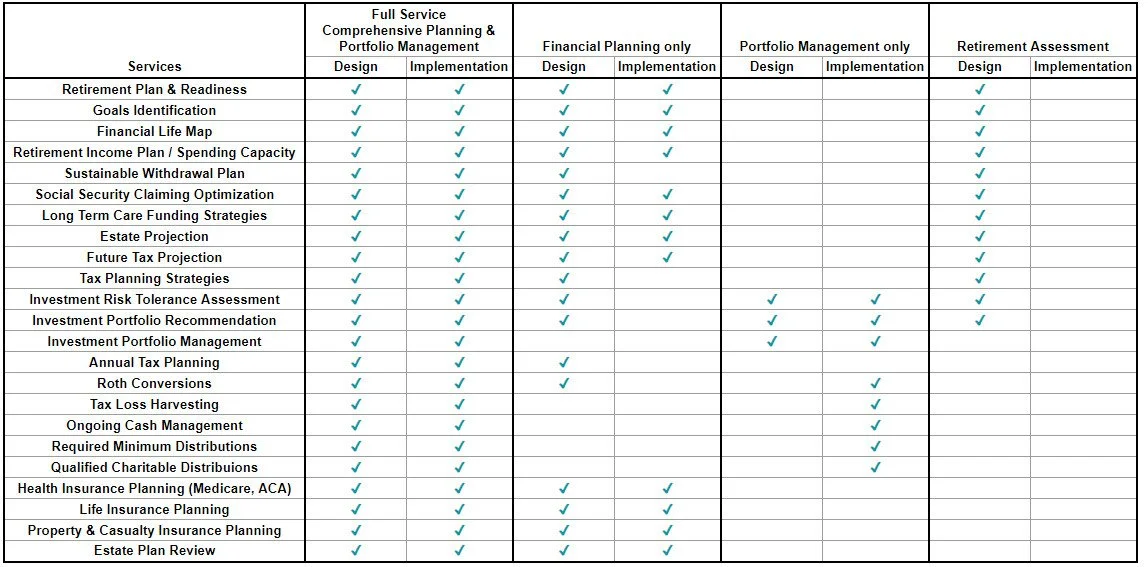
Ongoing Services
Service and Support
Stable Income Sources Alternative
Medicare Plan Options
Cash & Portfolio Distribution Management
Social Security Claiming Strategies
Pension Payout Options
Estate Plan and Beneficiary Review
Roth Conversions
Portfolio Withdrawal Strategy Review
Rebalancing of Investment Portfolios
Home Equity Strategies
Tax Planning
Long-Term Care Needs & Funding
Life Insurance Needs Analysis
Proactive Aging Planning
Qualified Charitable Distributions